Viruses, contract killers, poison and drugs: In the Darknet, trade in goods that many people only know from crime novels is flourishing. But what is the Darknet really? Is it the dark side of the Internet - or is it merely misused by criminals for their own purposes? Without the necessary software or a certain browser configuration, the darknet is invisible for ordinary Internet users. That's why the Darknet is sometimes referred to as part of the Invisible Web. Our guide will shed light on the darknet.
How do users remain anonymous?
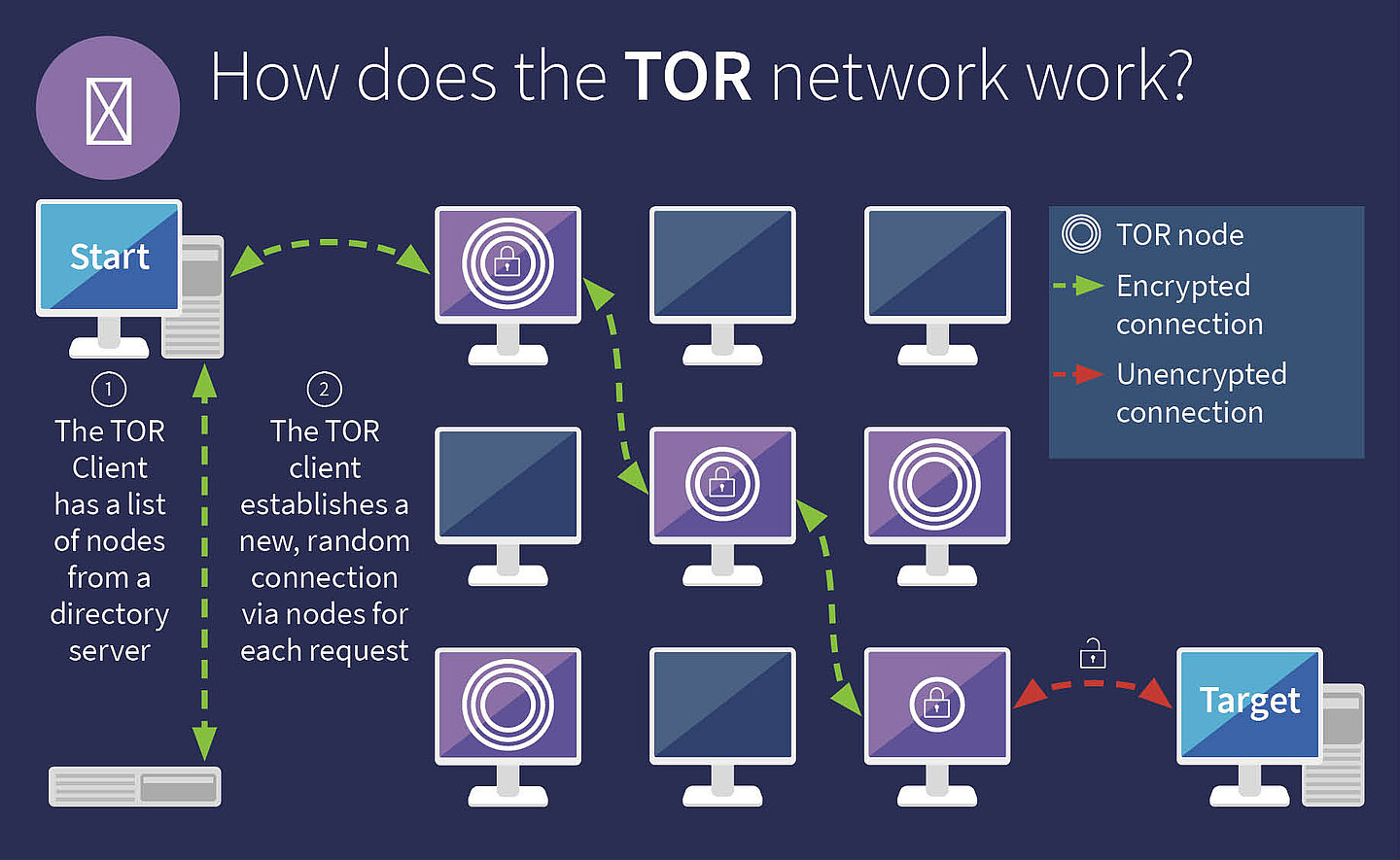
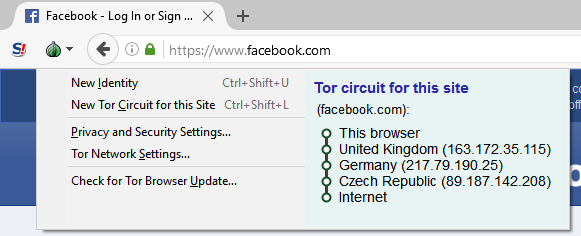
The secret world of the Darknet is not entered through any gate, but through the TOR: TOR stands for "The Onion Router". The word "onion" refers to the layers that must be penetrated by the data: Unlike normal surfing, the computer does not connect directly to the server where the website is located. Instead, a whole series of servers are involved in the connection in order to create the greatest possible anonymity.
The layers of the "Onion"
The starting point
Your journey to a Deep Web page starts on your computer
The first layer: Entry-Point
The entry point (Server 1) into the TOR network receives the IP address from your computer. The TOR client then connects your computer to another server (server 2), the node. All data is encrypted on the way to this node.
The second layer: TOR nodes:
The node (Server 2) only knows the entry node - but not your computer or your IP address. The data sent via this node is encrypted and therefore cannot be read by the node. In addition to the entry point, the TOR node only knows the exit node (Server 3), i.e. the server that finally connects you to the desired page.
The third Layer: Exit Node
The exit node (server 3) establishes the actual connection to the web server on which the requested target page is located. From the exit node, you can access the legitimate services that end in .onion. Outside the TOR network, services with the .onion extension are not accessible.
The target: Web server
This is where your journey ends - you have reached your destination. This is where the Deep web page you want to access is stored. This web server only knows the IP address of the exit node. The web server does not get to know the other servers or your computer.
The data packets between the laptop and the entry point are encrypted. The entry point receives the encrypted packet, repacks it, adds the address of the TOR node and its own sender IP address. Then it sends the packet to the TOR node, which basically does the same thing: It does not open the packet, but flags its own IP address as the sender and sends the whole thing on to the address of the exit node. In this way, the IP address of the source device remains secure, since the website only knows the address of the exit node and each of the individual instances only knows its nearest neighbor. This way, the user remains anonymous.
Of course, you can also access "normal" clear web pages via the TOR browser. With ordinary web pages TOR behaves like an ordinary browser. With deep web pages it looks a bit different: Given the complexity and high number of connections required, it's hardly surprising that accessing a deep web page takes much longer than accessing a normal website.
HTTP vs. HTTPS
HTTP
- HyperText Transfer Protocol (HTTP)
- Before the actual URL, the abbreviation HTTP appears at the top in the browser's address bar.
- The connection is not encrypted. Hackers have an easy time intercepting, reading and manipulating the data.
- The TOR browser puts an end to HTTP connections. Even after entering an HTTP address, the browser requests a securely encrypted HTPPS version of the page.
HTTPS
- HyperText Transfer Protocol Secure (HTTPS)
- The URL is preceded by HTTPS and usually a small padlock icon to indicate the security of the connection.
- To increase the security of HTTP connections, the SSL certificate has been added. The computers communicating with each other agree on a common key that protects the connection.
- The makers of TOR consider HTTP to be so insecure that they automatically attach a certificate to each HTTP connection, thus transforming it into an HTTPS connection.
Is the user fully protected with TOR?
The TOR browser and similar applications make the paths taken by the data anonymous. However, the data sent via it is not necessarily secure. For example, log-in data, credit card information or addresses can be extracted when entering data in a web form even if TOR is used. In addition, the anonymity of TOR communication can also be removed if someone gains access to the TOR browser, which can also be manipulated like any other software. The same applies, of course, to servers through which TOR directs users or on which Deep Web pages are stored.
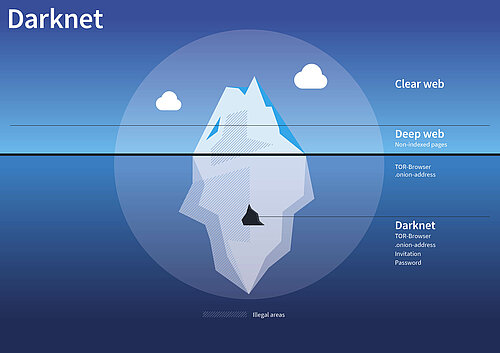
What is the difference between Darknet and Deep Web?
In the most of the popular German-language media, the terms Darknet and Deep Web are used synonymously. In reality, Darknet and Deep Web are by no means identical because the Darknet is only a small part of the Deep Web. Figuratively we can imagine the Internet like this: The ordinary Internet, which we can search with Google and Co., is the tip of the iceberg. The part under water that we can only see with special means is the Deep Web. And the Darknet is the underside of the iceberg floating in the sea.
To see the parts of the iceberg below the water surface, special "diving equipment" is required - the TOR-Browser. To get from the Deep Web to Darknet, a lot more is required. While the visible web - i.e. the familiar, visible and search engine driven Internet - is accessible with an ordinary browser, the deep web operates hidden beneath the surface of the network. To access the pages of the Deep Web you need encryption, the TOR network, which ensures anonymity while surfing. The only access key to the Deep Web is a specific software and the appropriate browser settings.
Who's using the darknet?
Anonymity is particularly interesting for two groups: On the one hand, there are people who need the protection of the Deep Web for their communications. They share sensitive data and information and have to fear for their own lives or those of their informants if they do not exchange information under the protection of the Deep Web. This group includes the politically oppressed or dissidents, opposition members from countries led by dictators or journalists and whistleblowers. Through the Deep Web, they can also access content that is not available to them on the visible web due to political restrictions, that is censored, or that would put the informant's life at risk.
Anonymization helps journalists protect their sources. For example, Arab Spring activists have been able to access social media channels through the TOR network and disseminate information about the revolution. Whistleblowers such as Edward Snowden also use the Deep Web to bring sensitive information to the public. This first group protects itself from negative consequences and persecution by fleeing to the Deep Web.
And the second group also uses the anonymity of the Deep Web to escape negative consequences - and escape prosecution. This group is made up of people whose activities on the visible Internet would very quickly lead to complaints, fines and imprisonment. Darknet includes forums, web shops and trading platforms for services and goods that are either illegal or subject to strict legal regulations.
And what are the criminals doing in the Darknet?
Unregistered weapons, drugs, forged and stolen documents or credit cards: In the Darknet there is everything that should not be available under the current law. Increasingly, IT experts with criminal ambitions are also offering their services in the Darknet. From overload attacks (DDoS attacks) designed to paralyze websites and Internet services to virus construction kits and spam campaigns - Darknet is a shopping paradise for cyber criminals. Payment is usually made in one of the numerous electronic crypto currencies, which are also designed for anonymity.
Many of the underground forums use a recommendation system to approve new merchants. New users are only admitted as merchants if they have been classified as 'trustworthy' by other, already active merchants. In some cases, customers also have to be approved by the operator, pay a "membership fee" or a deposit before they can see anything on the site and make purchases.
Since the users in Darknet move almost without trace, investigators can only track down the perpetrators behind the criminal offers, online shops or forums in the Darknet after lengthy research. For this reason, investigating authorities have founded special units whose task it is to penetrate the illegal areas of the Darknet. Classic surveillance work is also one of the tools used to catch the perpetrators: Drug deals, for example, are often carried out via packing stations, as in the case of "Moritz". The fact that access cards for the Packstation that have been stolen and sold in the Darknet are frequently used for such transactions makes the criminal web of the Darknet evident.
What is possible in the Darknet?
In the Darknet, everything is possible that is possible on the freely accessible Internet. In addition, the anonymity of the Darknet opens almost unlimited possibilities to offer illegal services, killings, weapons and drugs or to share or acquire pornographic content of any kind and videos of murders and abuse.
What you can buy on the Darknet:
Deadly poison
In the USA, this case made the headlines: A young man improved his pocket money with the production and sale of ricin. Ricin is a protein derived from a spurge plant that quickly kills human cells and can be fatal even in tiny amounts.
Credit card numbers
These may have fallen into the hands of criminals via phishing websites, keyloggers or classic card theft. With this data, the perpetrators can shop at the cardholder's expense. Usually the numbers are sold in bulk. This increases the probability that at least some of the cards are not yet blocked.
Weapons and ordnance
The Darknet contains almost everything that criminals are looking for. Among other things, relevant deep web sites offer explosives. In addition to C4 plastic explosives, rocket launchers and numerous other weapons can also be purchased on the Darknet.
Counterfeit identity cards
A Darknet site called "Fake Documents Service" claims to be able to offer stolen passports and documents from almost every country. A passport of a citizen from the USA is available there for less than a thousand dollars.
Marihuana
The question "How to buy weed on the Deep Web" leads to almost one million hits in the usual Google search. Where there is such a lively demand, there is also an almost inexhaustible supply: In the Darknet, dealers offer various types and forms of the drug. The same applies to various other drugs. Everything in circulation on the street has long since found its way into the Deep Web.
Forged university documents
The Darknet is known for its wide range of forgeries of all kinds. No wonder, then, that documents can be obtained there in a comparatively uncomplicated manner. However, this is not a speciality of the Deep Web: Criminals have long been offering all kinds of forgeries on the Internet, that can be found via Google.
Contract killers
In the Darknet there are numerous offers to kill a person for money. However, it is unclear how many of these offers are real or fake.
Viruses and malware
The Darknet also promotes cybercrime: With so-called crimeware kits, the perpetrators can configure viruses and malware according to their own wishes, without having any in-depth knowledge, with just a few clicks.
Uranium
In a world in which almost everything can be bought, it is hardly surprising that uranium ore, that can be processed into weapons, can also be obtained on the Darknet. The Washington Post has investigated such offers. The editors have found that the uranium ores that are available in small quantities on the Darknet are also available from Amazon.
Do I make myself liable to prosecution if I surf in the Darknet?
Search engines such as Grams, ahimia.fi and Torch help users to search the as yet unmanageable Darknet in a targeted way - just like Google and Co. facilitate the search for web content. Both searching and surfing the dark web can quickly become dangerous: Even without buying illegal goods and services, Darknet users can make themselves liable to prosecution if the thumbnails, i.e. the small preview images of the search results, end up in the browser cache and are thus stored on the computer - even if only temporarily. If investigators find such thumbnails of illegal content such as child pornography, this is enough for prosecution. In order to avoid this, users usually use a virtual private network (VPN) that prevents the incidental storage of data. The actual surfing in the Darknet is therefore not illegal per se - it depends on what you do there.