The first computer viruses were developed in the 1980s. Soon after, programs were also created that could keep them under control. In 1987, G DATA led the way and developed what was probably the first virus scanner in the world. This virus scanner went on to become a cornerstone for traditional security solutions. It uses so-called signatures to check your computer for viruses, worms, Trojans and other malware.
How do virus scanners work?
Viruses need a host, so they infect files that already exist on the computer. Worms, on the other hand, can distribute themselves without such a host and often without the help of the user. Trojan horses often hide their malicious intentions in programs that appear to be legitimate – in much the same way as the historical wooden horse. Every piece of malware functions differently and can therefore be broken down into almost countless further subgroups. But despite the extensive range of malicious programs, patterns can be detected. They exhibit malicious features in their code – and the virus scanner can use these to precisely identify them.
The virus scanner uses signatures to track down Trojans, spyware and other software circulated by criminals. These are generally comparable with detailed profiles that the virus scanner uses to scan the files on a computer, a bit like an electronic sheriff. If the features stored in the signature match those of the suspected intruder, the virus scanner pounces immediately and “arrests” the malware.
What do virus signatures look like?
But “sheriffs” in the world of cyber crime don’t have it all their own way like those in the Wild West. In the digital age there is no single, well-described bandit causing trouble. That is why today’s signature profiles very frequently do not relate to a single malware strain. Rather, the signature also provides the ability to detect a wide range of files that contain code into which known malicious features are embedded. The keyword here is heuristics.
The cyber sheriff is not just looking for a 30-year-old man with a large moustache and a black hat. He is looking for a man between 20 and 40 with some facial hair and numerous other features. This special type of virus signature sets different priorities to the detailed Wild West profile. While the profile lists few but very specific features, the more extensive virus signature includes a large number of typical points that are each somewhat vague. Correspondingly, the cyber sheriff does not generally determine one villain but can often find up to thousands of dangerous files using one signature. However, increased caution is advised here too. If the features are described vaguely, it is possible for a file to be incorrectly classified as suspicious – a so-called false positive detection.
In technical terms, this means that the heuristics are based on less specific data, rather than using virus signatures tailored to a specific malware strain. This includes, for example, knowledge of general patterns that a great number of malware strains are known to display. Furthermore, the heuristic method checks whether specific code elements are capable of causing problems when combined with other features. Consequently, a heuristic process can intervene proactively, even before a very specific signature is available.
What does it mean when a virus scanner works “reactively”?
A virus scanner in the traditional sense can only detect things that analysts have “taught” it in advance in the form of signatures. If there is no signature for a malicious file, this basic approach cannot work. Therefore, experts refer to virus scanners as working reactively – they are based on a reaction to the analysis of malware that has already been encountered. The virus scanner can only go on the hunt for these once a signature has told it what the opponent looks like. For this reason, virus scanners should only be seen as basic protection or as an enhancement to a more comprehensive security solution.
How often should I update my virus scanner?
Analysts can generate virus signatures comparatively quickly. Hence every signature update increases the virus scanner’s inventory of viruses it has on file. Regular updates are crucial to enable the digital sheriff to detect as many profiles as possible. In this way, the virus scanner becomes aware of more and more new malware strains and can trace them in your system. G DATA security solutions carry out automatic signature updates.
What happens when the virus scanner finds something?
If the virus scanner has found an instance of malware, it can either disinfect it, put it in quarantine or delete it. In many cases, infected files can be recovered. With disinfection, the antivirus software removes the malicious components in the infected file and hence reconstructs the original file. If the disinfection is successful, the file is automatically moved back to its original location and can once again be used as normal.
If the disinfection fails or it is not clear if a file is infected, the software puts it in quarantine. It cannot cause any damage here, and the infected file is still available for possible repair attempts. By quarantining a file any risk to your computer is eliminated. The quarantine option is also helpful if system files appear to be infected. The system may be damaged if they are simply deleted. If the computer continues to run without any problem while the file is in quarantine, the file in question may just be deleted later if necessary.
How do I switch off my virus scanner?
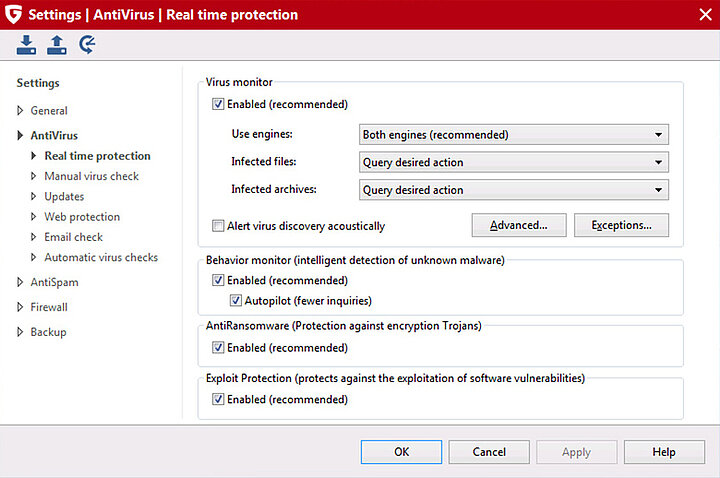
You can find the individual components of your G DATA security solution listed under “Settings” and “AntiVirus”. If you click on the components, you can enable or disable them by unticking the check box at the very top of the window. Although it is of course technically possible to switch off the virus scanner, it is not recommended. The virus monitor’s real-time protection thoroughly checks your computer for threats and as such should be left enabled at all times.
Does my smartphone need a virus scanner as well?
A smartphone is basically a pocket version of a computer. Your smartphone can become infected in the same way as your computer. For this reason, it needs similar protection.
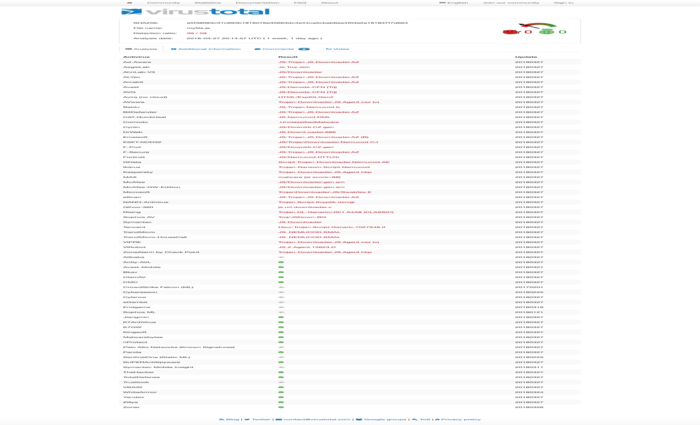
What do online virus scanners such as VirusTotal do?
Whereas the majority of virus protection programs are downloaded onto the local computer, there are online alternatives for a signature-based scan, such as virustotal.com or virscan.org. Online scanners such as these analyse individual files or scan a URL selected by you for dangerous content – without the need to install a program. Over 40 providers of antivirus software have made available their engines (for files) in the basic version and a section of their Cloud technologies (for URLs). VirusTotal and the like provide a list of whether and which malware has been found by the respective virus scanner at a specific point in time. For this reason, online scanners are also called “second opinion scanners” that provide a second opinion – or over 40 additional opinions – on a discovery. They scan a file, but do not prevent an infection and cannot help with removal.
However, the snag with such an online scan is that you upload the data to a remote server. Whether you are creating more security or just voluntarily handing your data over to strangers is questionable. Furthermore, if none of the online scanners listed find anything, this doesn’t automatically mean all is well! Many malware strains are either well disguised against signature detection or are only apparent through their behaviour. Hence such online scanners do not offer any alternative to a comprehensive security solution.