Imagine you are sitting in a café and you connect your smartphone to the available Wifi network. Did you know that people can read anything unencrypted that is transmitted on this network? Criminals use special spyware for this that can intercept the data traffic. This enables them to access user names, emails and chat messages. Many apps and websites make it difficult for you as a user to find out whether or not all outgoing and incoming data is encrypted. So it is more secure to rely on VPN software. This generates a virtual private network (VPN) in which your data remains protected along the transport path. You can find out here precisely how this works.
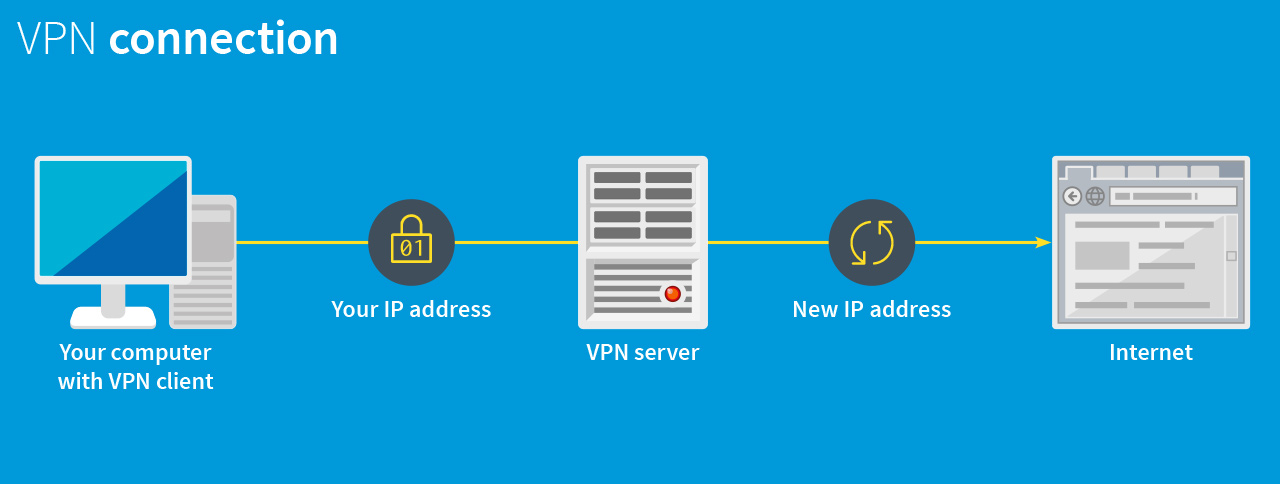
How does a VPN work?
When you use VPN software, you do not connect directly to the Internet as usual. You first establish an encrypted connection to the VPN provider, who in turn forwards you to the Internet. Your data is anonymised by doing so. Because your connection request is sent via a server belonging to the VPN provider (hub), you are allocated a new IP address as the user. This protects your real IP address, which is used to identify your device. The virtual private network makes your computer invisible.
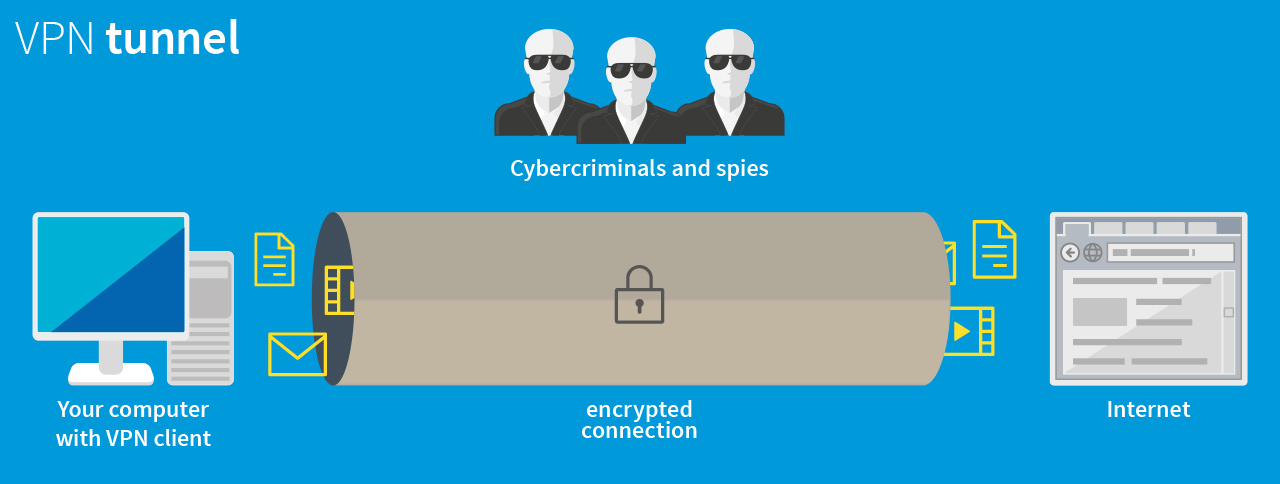
So what is a VPN tunnel?
The image of a tunnel is a good way of illustrating how a VPN works. From outside a road tunnel, nobody can see or influence the traffic inside. It is the same with a VPN connection: nobody else can see the data being transferred, as the connection is encrypted. In fact, an attacker can see that a connection has been established via this tunnel, but he cannot see what is being sent, or where to.
Setting up a VPN
To use a VPN tunnel, you need to install a specialized piece of software called a "VPN client" on your notebook, smart phone or tablet. This client software provides a connection to a VPN provider.
As a user, all you need to do is install the VPN program or the app and activate it with just a few clicks. The client software will take care of the rest. In some cases, a VPN node is preconfigured, in which case you just need to specify the point to which you would like to connect. For instance, by selecting a country, you specify the location of the VPN server you connect to. As soon as the connection is established, you can use your device as usual.
VPN stands for "Virtual Private Network"
Why do I need a VPN?
Whenever you are on a network that cannot be trusted it makes sense to use a VPN. This may be the case for example with a WLAN at an airport, at a conference or in a hotel. In such networks, there is a high risk of an attacker stealing personal data such as passwords or credit card numbers, or reading your emails and instant messages.
Where is a VPN used?
Companies rely on VPNs, too, when confidential data needs to be transferred. They use it to enable field-based staff to access data that is otherwise only available via the office network. The company provides a node that can be reached via the Internet and that the staff can connect to. This node acts as the link between the client in a public network or home network and the internal company network. It enables staff who are out of the office to work with peace of mind, exactly as if they were in the office – the data cannot be seen and is transferred securely.
More information and sources
- G DATA Mobile Malware Report H1/2016
- G DATA Security Blog: “HummingBad“ – Money-making Malware, Made in Asia
- G DATA Mobile Internet Security for Android





