In its original form, a firewall is protection technology that separates areas of a network from one another. In practical terms, this generally means that it keeps an eye on all incoming and outgoing data packets. It is a kind of digital gatekeeper and checks that these data packets are only sent in and out when they are actually permitted to. When doing so, the firewall works according to predefined rules to open, block and monitor the inbound and outbound access points (ports) as needed.
Why do I need a firewall?
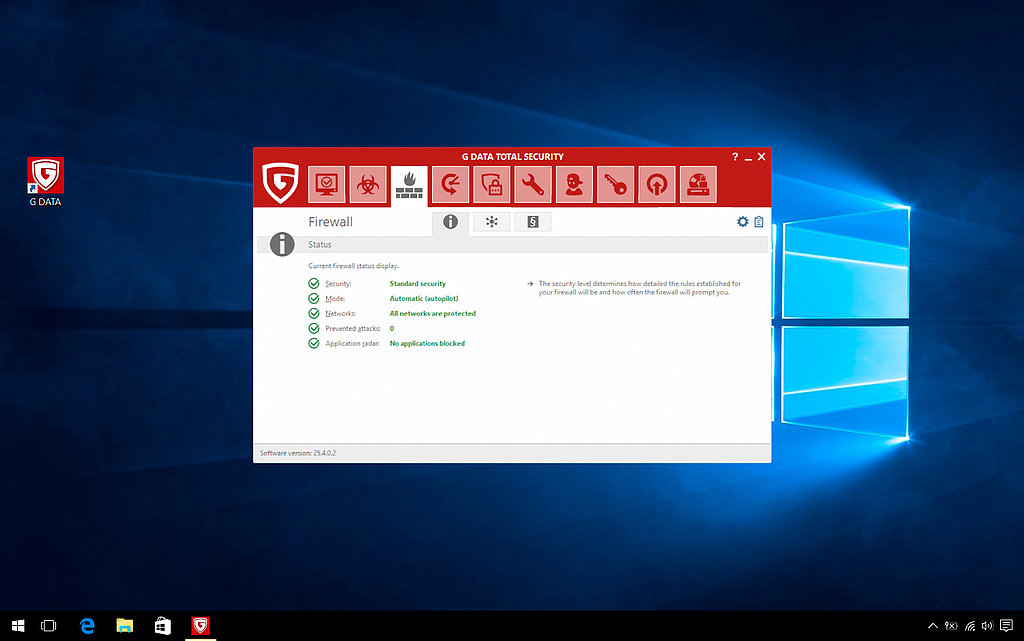
Put briefly, using a firewall is a practical, important element of a sophisticated security concept. It ensures that no network traffic can rush past you without authorisation. Only absolutely essential access should be permitted. If an inbound connection does not correspond either to a request from inside the network, or is not associated with a service that is open to the outside world, access is denied.
In this way, attacks from outside are fended off, for example, where attackers try to use open ports to gain access to a network or a computer. If a computer is directly connected to the Internet - which was usually the case in previous years - attacks and infections could be carried out within seconds. Internet worms such as SQL Slammer, Sasser and the like would have been stopped by a firewall. Today such malware is hardly ever successful, as firewalls and routers have corresponding filter mechanisms and the malware cannot even get into the system.
Many users do not want to get too heavily involved with which ports and how many of them are open on their computer. A firewall is a good choice for them - it means they no longer have to think about the access paths to their system and can leave the protection to the firewall. To guarantee security, you should generally not switch off the firewall.
However, traffic from inside to outside can also be blocked, for example if malware tries to make contact with a control server and this process contravenes a set rule. Depending on the type and configuration of the firewall, it can differ greatly in the way it contributes to monitoring the network traffic.
Where do I find the firewall?
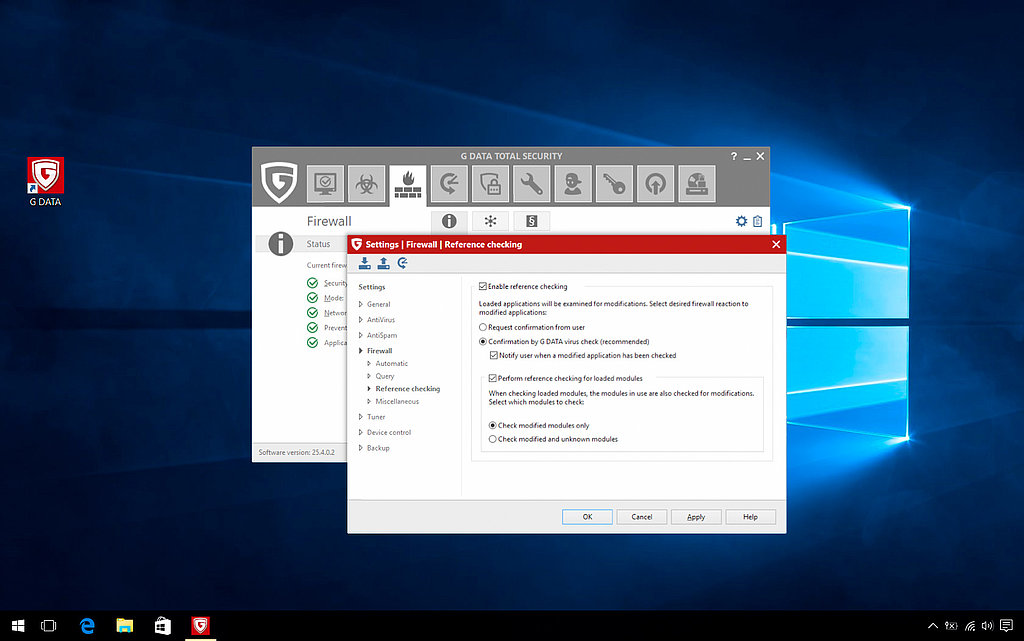
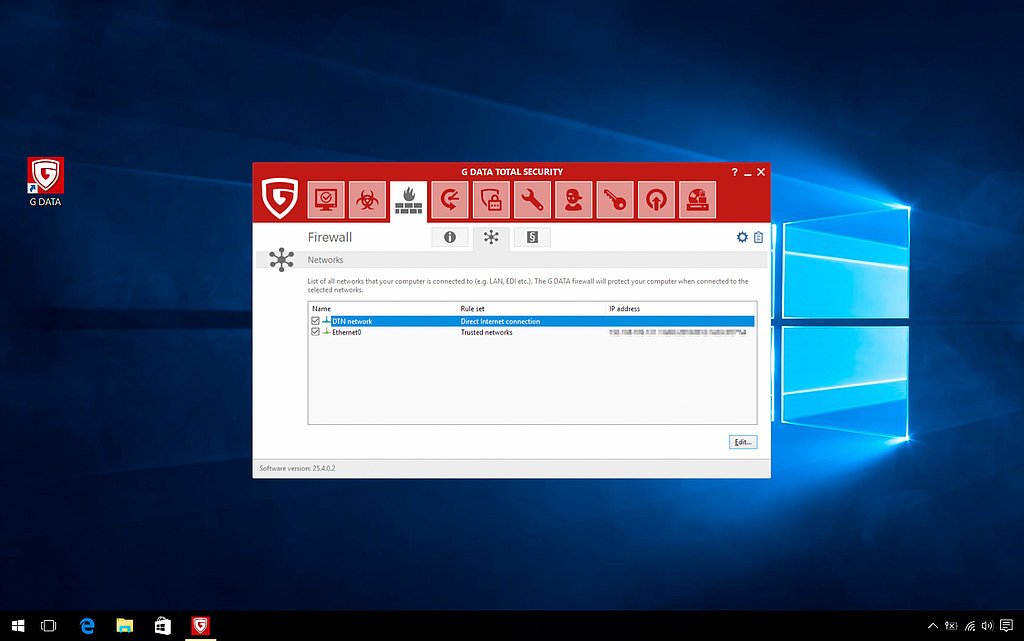
This depends entirely on the structure of the network. In a home network, firewalls are generally found on the computer itself as part of a comprehensive security solution. This is called a personal firewall, desktop firewall or software firewall.
In addition to this, many modern routers are also equipped with firewall functions. If you use such a router, you are moving part of your line of defence one step forwards - your router checks the network traffic before it even gets to the devices on the home network. Such a router is simply known as an external or hardware firewall.
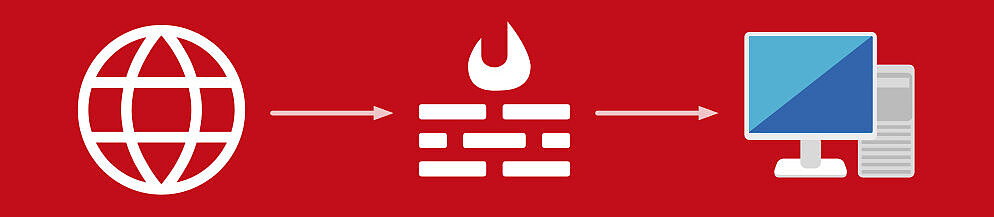
Hardware firewalls are commonly used in corporate networks as well. They form a protective wall between the outside world and the corporate network. They are significantly more comprehensive – and are dedicated to this specific purpose. Additionally, firewalls (hardware, software or virtual networks) are used to subdivide large networks into smaller segments and so create controlled access points. So, for example, the accounting areas are separated from production, portable devices from the corporate network and much more.
What does a firewall do?
The following explanations will give an extremely rudimentary view of the various functions of firewalls. To make it easier to understand, we will stay with the image of a gatekeeper dealing with incoming packets.
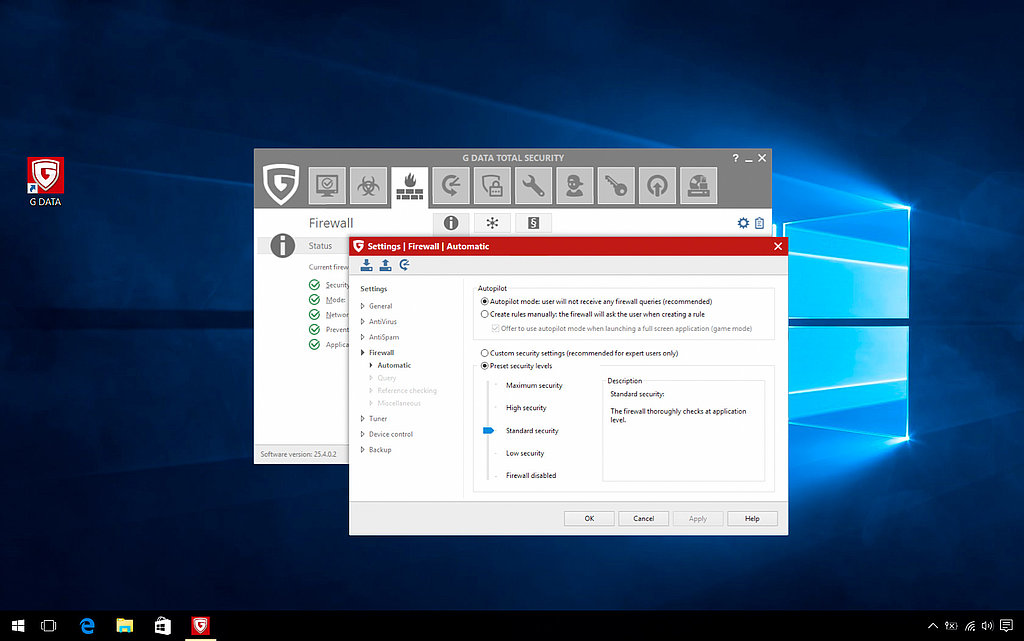
Standard firewalls have what are called packet filters. Figuratively speaking, they look at the address label on each data packet and use a static rule set to decide whether it should be allowed in or out. This function is fundamental to all firewalls.
A further level of development is what is called stateful inspection, which is also described as dynamic packet filtering. The static rules here are expanded and, put briefly, enhanced to check the connection status. In a manner of speaking, it checks whether the recipient of a packet is prepared to receive it and can and wants to accept the packet. If a connection is successfully established, this is also subject to specific rules and is strictly monitored.
The next optional stage is filtering data streams at the level of applications, also called a proxy firewall. Here the packets are not only viewed and passed on, but also checked for their contents. This process is known as deep packet inspection. In doing this, multiple packets can be held at the entrance if necessary until their legitimacy has been established; then they can be forwarded to the recipient. Active website content is frequently blocked by rules in the proxy to prevent the computer from being infected.
Enhancement options for a complex firewall include modules for detecting unauthorised access (Intrusion Detection System or IDS) and preventing unauthorised access (Intrusion Prevention System or IPS). A firewall can also be the endpoint for a VPN tunnel.